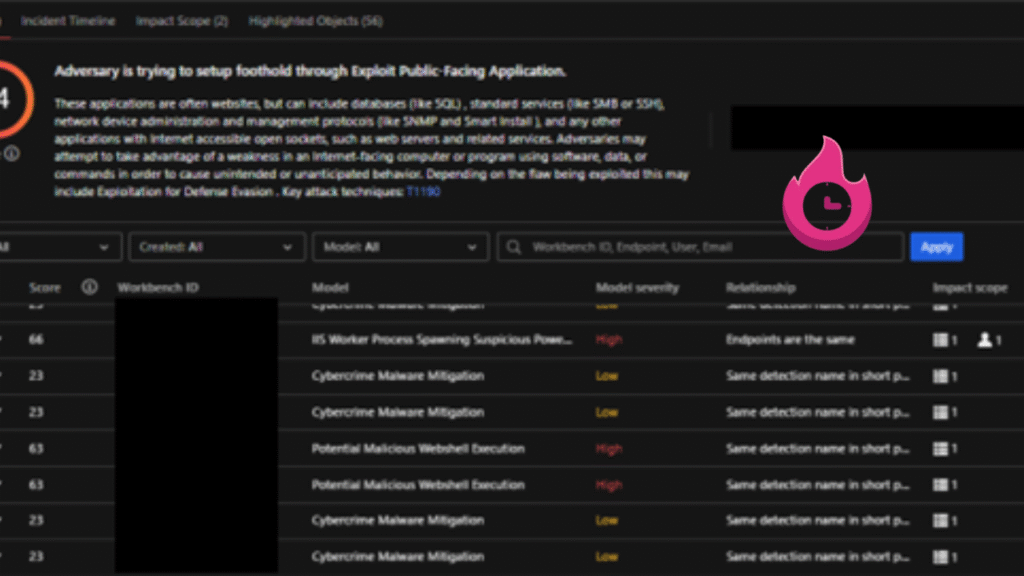
If you’ve ever searched about computer hacking or cybersecurity, you might have stumbled across terms like Mimikatz or timeline snippet. These sound technical and intimidating, but don’t worry. In this simple guide, we’ll break down exactly what a Mimikatz-centric timeline snippet is, why it matters, and how it connects to real-world cyber attacks. You’ll also learn how hackers use Mimikatz to steal passwords and how you can stay protected—even if you’re not a tech expert.
What Is a Mimikatz-Centric Timeline Snippet?
Let’s break this term down step by step.
Mimikatz is a well-known cybersecurity tool created to show vulnerabilities in Windows systems. Originally built by Benjamin Delpy as a proof-of-concept, it unintentionally became a favorite among hackers because it could extract passwords, hashes, PIN codes, and Kerberos tickets from memory.
A timeline snippet in this context refers to a small but crucial piece of information in a timeline of events involving Mimikatz. Imagine a digital diary where each entry marks when Mimikatz was discovered in a cyber attack, used in a breach, or updated to bypass new security measures. A Mimikatz-centric timeline snippet focuses on those key moments, helping analysts and researchers understand how the tool has evolved and been abused over time.
Think of it like a highlight reel of Mimikatz’s life in the cybersecurity world—short pieces of a bigger story that together reveal how devastating and persistent this tool has been.
Why Do Hackers Use Mimikatz?
Hackers love Mimikatz because it gives them direct access to one of the most valuable assets in any system: passwords.
When you log in to your Windows computer, the system often stores your credentials (like passwords) in memory so it can reuse them. Mimikatz can pull these credentials out, even if they’re encrypted, and hand them over to an attacker.
But there’s more. Hackers also use Mimikatz for:
- Pass-the-Hash attacks: This allows them to use a password hash to authenticate without needing the actual password.
- Pass-the-Ticket attacks: Here, attackers use Kerberos tickets stolen with Mimikatz to access other systems in a network.
- Dumping passwords in clear text: Yes, Mimikatz can even pull out plain-text passwords in certain cases.
For a hacker, it’s like finding a master key that opens every door in a building.
Password Stealing Made Easy
One of the scariest things about Mimikatz is how easy it is to use. You don’t need to be an elite hacker; even someone with basic knowledge can follow tutorials online and start using Mimikatz.
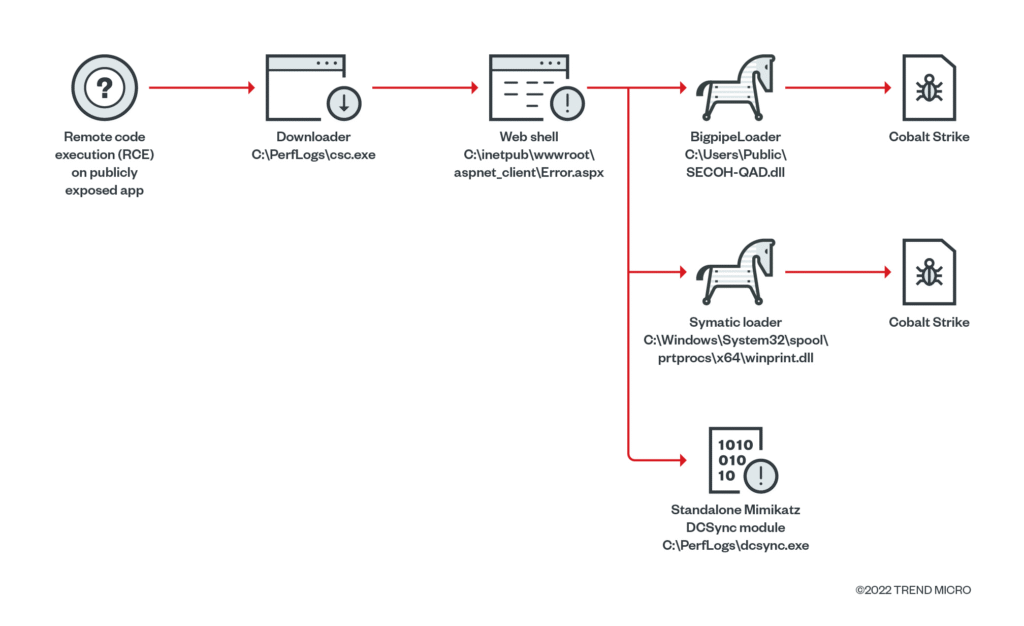
Once deployed, Mimikatz operates silently in the background. It scans Windows memory for login details and dumps them for the attacker. This is especially dangerous in corporate environments where one stolen password can lead to an entire network being compromised.
Breaking Windows Security
Mimikatz exploits weaknesses in Windows authentication mechanisms like LSASS (Local Security Authority Subsystem Service). LSASS is supposed to keep your login credentials secure in memory, but Mimikatz can hook into it and extract sensitive data.
Even though Microsoft has patched many vulnerabilities over the years, attackers still find ways to bypass protections using updated versions of Mimikatz.
A Tool Loved by Hackers
Mimikatz is open source and free. This accessibility makes it a go-to tool for penetration testers (ethical hackers) and cyber criminals alike. Red teams use it to test security in a controlled way, but threat actors use it to wreak havoc.
It’s been included in popular hacking frameworks like Metasploit, Empire, and Cobalt Strike, making it even more widespread in attack campaigns.
How Does a Timeline Snippet Help?
Timeline snippets help cybersecurity professionals track how Mimikatz has been used in past attacks. By analyzing these small events, they can:
- See how attackers adapted Mimikatz after security patches.
- Learn from major breaches where Mimikatz played a role.
- Build better defenses by predicting future attacker behavior.
It’s like piecing together a crime scene, where even small clues can lead to big breakthroughs.
Key Events in Mimikatz History
Here are some important moments in the life of Mimikatz:
- 2007: Benjamin Delpy starts working on Mimikatz to demonstrate Windows vulnerabilities.
- 2011: Hackers begin using Mimikatz in targeted attacks.
- 2014: Mimikatz becomes part of multiple APT (Advanced Persistent Threat) toolkits.
- 2017: Mimikatz plays a crucial role in global attacks like WannaCry and NotPetya.
- 2020–2023: New Mimikatz versions emerge, bypassing updated Windows protections.
Each of these events represents a Mimikatz-centric timeline snippet that security teams analyze to strengthen defenses.
Mimikatz in Real-Life Attacks
Mimikatz isn’t just a theoretical tool; it’s been used in many high-profile cyber attacks.
For example, APT groups (state-sponsored hackers) have relied on Mimikatz for lateral movement—spreading from one computer to another in a network. Even ransomware gangs use it to escalate privileges and gain access to sensitive data before encrypting it.
WannaCry Ransomware
In 2017, the world witnessed one of the largest ransomware outbreaks ever: WannaCry.
Mimikatz was a key component in WannaCry’s spread. Once the ransomware infected a system, Mimikatz helped it steal credentials and move laterally across networks, locking down entire organizations. Hospitals, banks, and governments were hit, causing billions in damages.
NotPetya Attack
Later the same year, NotPetya emerged—a destructive malware campaign that paralyzed businesses globally. Like WannaCry, it leveraged Mimikatz to gain administrator privileges and propagate quickly.
Unlike WannaCry, NotPetya wasn’t even trying to make money; it was designed to destroy data. Mimikatz was the silent enabler behind this devastation.
How to Protect Against Mimikatz
Stopping Mimikatz requires a multi-layered approach:
- Keep systems updated: Install Windows security patches promptly.
- Use Credential Guard: Windows 10/11 Enterprise offers protection for credentials in memory.
- Apply the principle of least privilege: Don’t give users more access than they need.
- Monitor LSASS access: Use tools like Sysmon to detect suspicious activity.
- Educate employees: Social engineering often delivers Mimikatz to systems.
Small Pieces That Tell Big Stories
Each timeline snippet—whether it’s a minor update to Mimikatz or its role in a breach—helps paint the full picture of how this tool evolved from a proof-of-concept into a global threat.
For security researchers, studying these snippets is like reading the footprints of attackers in the digital snow.
Thoughts on Mimikatz Timeline Snippets
Understanding Mimikatz-centric timeline snippets gives us insight into how attackers work and how tools evolve. It’s not just about history; it’s about anticipating future threats. These snippets act as warning signs, telling us where to strengthen defenses before the next big attack.
The Bottom Line
Mimikatz started as a harmless experiment but became a hacker’s favorite weapon. Its timeline tells a story of how quickly the cybersecurity landscape can change. By studying Mimikatz-centric timeline snippets, we can learn valuable lessons to defend against tomorrow’s attacks.
The key takeaway? Stay vigilant, keep systems updated, and never underestimate the power of small pieces of information—they could be the difference between stopping an attack or becoming the next headline.